By following these steps, you should have a fully functional Kubernetes environment running locally on your Windows machine. This setup provides a great way to learn and experiment with Kubernetes and its various features.
Tag: Devops
Expanding EKS Cluster Management with Production Namespace and User Access
By following this guide, you have now expanded your EKS cluster management to include a production namespace and configured IAM and RBAC to securely manage user access. This setup ensures that your production environment is well-isolated and that users have the appropriate level of access based on their roles. Understanding and implementing these configurations is crucial for maintaining a secure and efficient Kubernetes environment.
Managing an EKS Cluster with Vagrant, AWS, and Kubernetes Tools
This comprehensive guide covers the advanced setup and management of an EKS cluster, including cluster creation, scaling, autoscaling, and role-based access control. By following these steps, you can efficiently manage your Kubernetes infrastructure, ensuring scalability, security, and operational efficiency. As a DevOps professional, mastering these tools and workflows is essential for effective infrastructure management and deployment automation.
Setting Up and Managing a Kubernetes Cluster Using Vagrant, AWS, and Kubernetes Tools
This detailed guide covers setting up a Vagrant VM, configuring AWS CLI, and installing essential Kubernetes tools (eksctl, kubectl, and Helm). These steps provide a robust environment for managing Kubernetes clusters and deploying applications efficiently. As a DevOps professional, mastering these tools and workflows is crucial for effective infrastructure management and deployment automation.
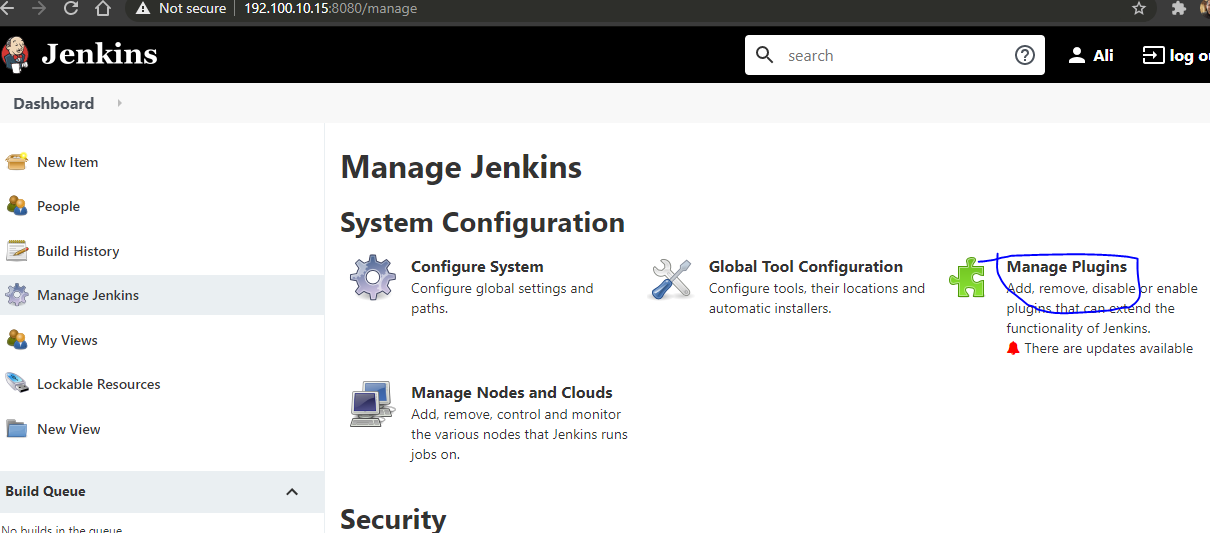
Jenkins, an Autonomous Java-based Application
The installation and configuration of Jenkins on a Linux server necessitate the presence of Java. Following a structured sequence of commands, Java is first installed, then Jenkins is downloaded and set up. Post-installation, accessing the server involves retrieving the initial administrative password for further configuration.